Do not Underestimate Doing This in Memory Forensics

The Scenario
Imagine that you are investigating a breach case and you took a memory dump of the suspect device. You are analyzing the memory dump, checking the processes, which one might be malicious, and DOING EVERYTHING that you should do.
The Overlooked Crucial Step
You reached to the part of checking the network connections using networking Volatility plugins like (netscan, netstat, connections, sockets, connscan) to identify the malicious IP/C2 server. That’s great step towards your investigation. However, I noticed a lot of people doing that, checking the ports, processes, but forgetting to check the reputation of the IPs in the first place! This will air your investigation and help you minimizing the spent time on figuring out what are the malicious IPs!
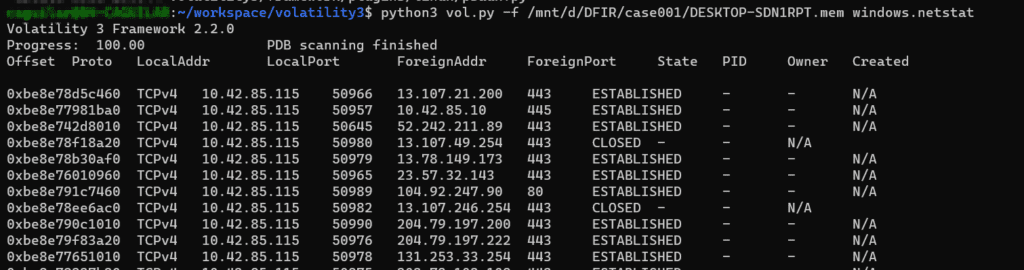
Well, for sure, if it is a public IP, you can check it, but for private IPs, you cannot do this step. This may be an insider threat or zombie case (a hacker controlling an enterprise computer) is here. Later on, if you got some public IPs, you may check them.
Caution
Please before inserting any IPs into such websites, check if that is ok with your management. In many cases, it is NOT ALLOWED to check with public reputation centers, especially in confidential cases!
My Recommendation
You are doing great by reaching to this point, but please remember to scan the found IPs with your local threat intelligence center first, then with public known IP and Domain Reputation Center (if allowed). I will list a few famous ones as examples:
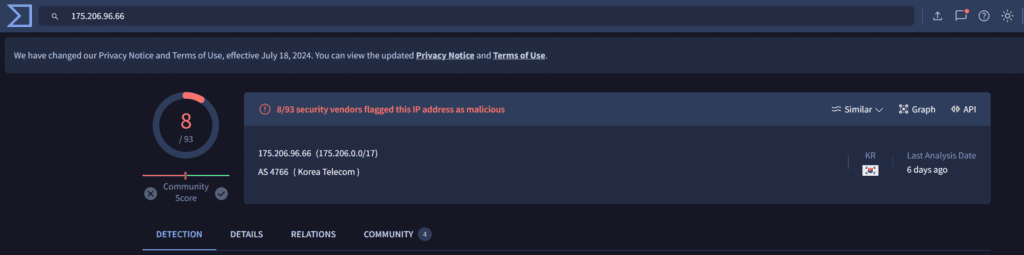
Conclusion
We talked about checking IP reputation using different IP reputation search engines in the chaos of investigating a security incident, so do not forget to do it if allowed 🙂
~ Cya in the next one