Windows Process Genealogy (Hierarchy)

What is Process Genealogy?
In the Technology world, Process Genealogy refers to the hierarchical relationship between processes running on a operating system. It involves understanding how processes are created, how they relate to each other, and the structure of parent-child relationships among them.
Understanding processes genealogy is crucial in the context of memory forensics. Today’s tutorial will shed some light on Windows Process Genealogy.
Why It is Important?
By knowing which process created which process, and understanding the relationships between them, a digital forensics examiner can identify and spot malicious ones. The would also gives additional details to the examiner as below:
- Trace Execution Flow: Knowing the genealogy helps trace the execution flow of processes, revealing how a malicious process was initiated and what other processes it may have spawned.
- Identify Anomalies: By analyzing process trees, forensic investigators can spot irregularities, such as legitimate processes being hijacked or unexpected parent-child relationships indicative of malware.
- Reconstruct Events: Process genealogy assists in reconstructing the timeline of events during a security incident, helping investigators understand the sequence of actions taken by malicious software.
- Correlate Artifacts: It allows the correlation of various system artifacts (e.g., logs, registry entries) with specific processes, enhancing the accuracy of forensic analysis.
- Support Legal Proceedings: Detailed knowledge of process genealogy can provide concrete evidence in legal proceedings, showing how and when a system was compromised.
How It is Done Using Volatility?
In Volatility2/Volatility3, there is a plugin called pstree, which is available for Windows, Linux and MacOs. In today’s tutroial, we will focus on the one related to Windows.
Windows Pstree helps us analyze the process hierarchy of a Windows system from a memory dump by visualizing the parent-child relationships among running processes at the time the memory image was captured.

The above snippet is from Volatility3, where I listed the available plugins, using the command:
python vol.py -hUnderstanding the Format of Pstree Plugin
If you are new to memory forensics, understanding the pstree plugin format might be confusing, so I will break it down as follows:
The format is about a tree, parent and children, where each process has two cases, either it has a dot (.) or asterisk (*) next to it – regardless of the number of dots/asterisks, or it does not have. If the process is without (.) or (*), meaning it does not have a clear parent. So, every user-mode process should have a parent process, meaning it was created by another process.
You might also see that some processes are children for a process, but also a parent for other processes like “services.exe” in the below snippet.
Look at the below snippet from a real memory dump.
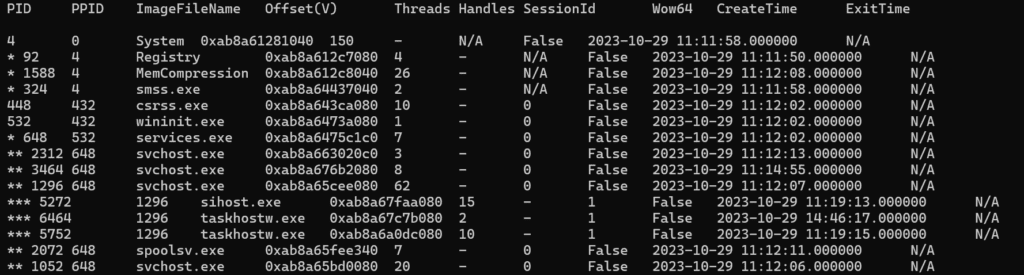
Note: Using Volatility in Linux environments gives clearer and more organized output compared to Windows ones.
What we can noitce from this snippet:
- “System” process is without (.) or (*) next to it, so it does not have a “clear” parent, but it has a parent with PID 0 (System Idle Process)
- “Registry”, “MemCompression”, and “smss.exe” processes are children to the “system” process (system is their parent process). Why? Because system process do not have (*) and under it, there are “Registry”, “MemCompression”, and “smss.exe” with 1 (*) next to them. Also, you can make sure that this is correct by examining their Parent Process Identifier (PPID 4) which matches the “system” Process Identifier (PID 4).
- “csrss.exe” and “wininit.exe” have Process Parent ID (PPID) as 432, which does not exist not in this snippet, not in the full output. Why? Because, smss.exe had another instance (PID: 432), which created “csrss.exe” and “wininit.exe”, then it got terminated. So, the real parent of them is the terminated instance of “smss.exe” process. How can I know? Continue reading and you will know too!
- “services.exe” has one (*) under “wininit.exe”, so “services.exe” is a child of “wininit.exe”
- 3 instances of “svchost.exe” process with 2 (*) next to them, are initiated by “services.exe”, so “services.exe” is their parent.
- “sihost.exe” and 2 instances of “taskhostw.exe” with 3(*), meaning they are children of “svchost.exe” instance with (PID: 1296)
- “spoolsv.exe” and another instance of “svchost.exe” (PID 1052) are with 2 (*). If we observe correctly, we can look up and notice that one process with 1(*), which is “services.exe” the parent of them.
As we already saw, there are cases where processes do not have a clear parent. This can happen for several reasons:
- System or Kernel Processes: Some processes are created by the system kernel during the boot process, such as the “System” process in Windows. These do not have a parent process in the traditional user-mode sense.
- Orphaned Processes: A process might appear to have no parent if its parent process has terminated.
- Process Creation Issues: If there were issues with process creation like security/permission issues, it might affect how the parent-child relationship is recorded and displayed.
- Volatility Plugin Limitations: Sometimes, the tools and plugins used for memory analysis, like Volatility, may not perfectly reconstruct all relationships due to limitations in the memory dump or inconsistencies in the data.
Usually, it is the first two cases.
Based on the Parent-Child Relationship, How Can I know if this is a Malicious Process or not?
Well, some processes are always initiated by the the same parent, for example, “services.exe” is always initiated by the parent “wininit.exe”. Otherwise, something malicious is happening.
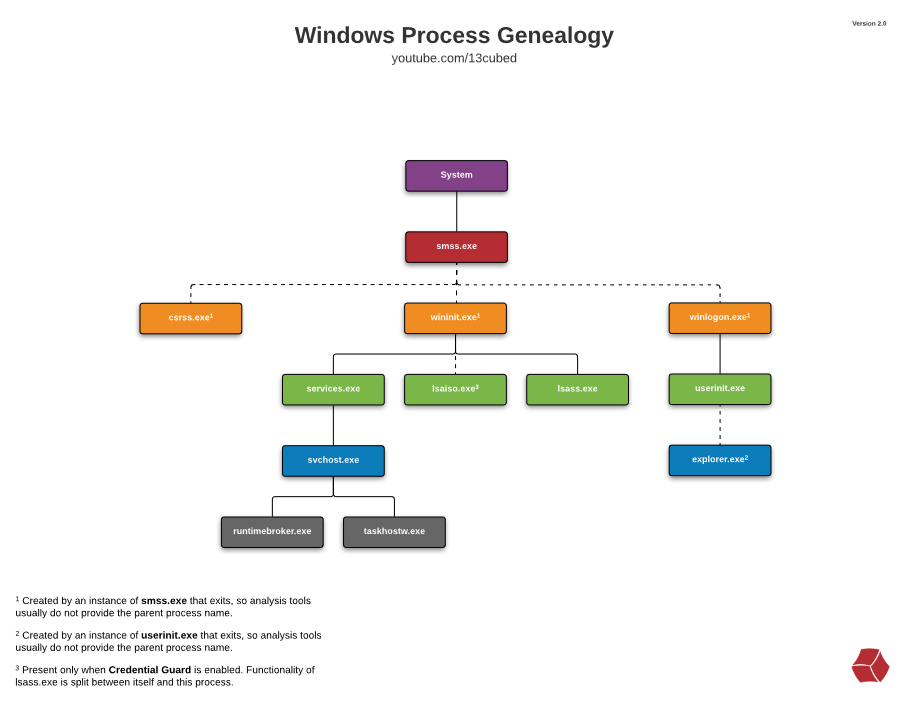
There are some documents, which show some parent-child relationships in Windows processes. For example, 13Cubed’s Windows Process Genealogy (Version 2.0) as below:
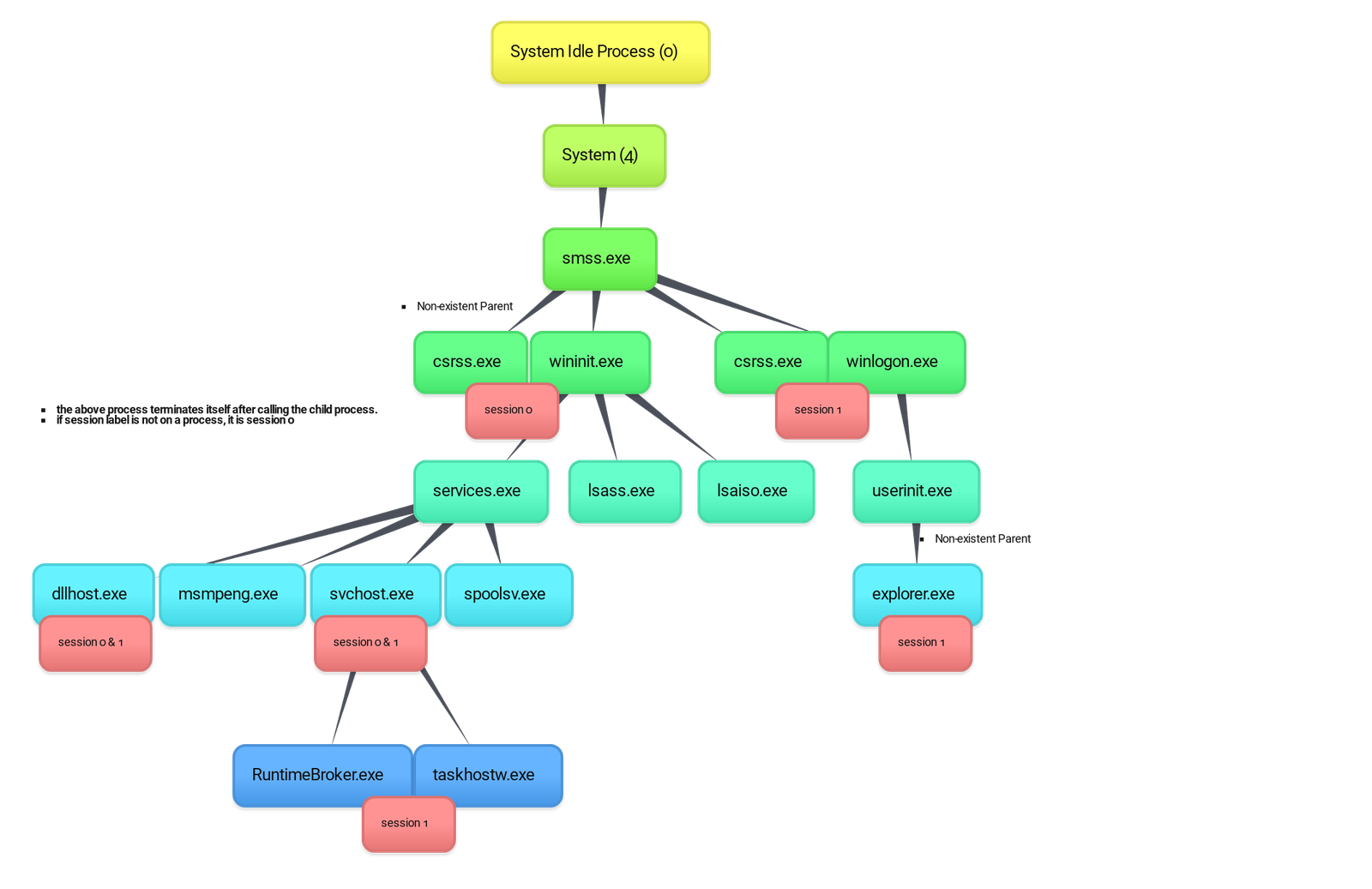
I also created one document “Core Windows Processes” based on a relevant room from TryHackMe, as below:
I also made a picture showing the relationships:
To know more about Windows Processes, there is a very good document “The Windows Process Journey” that lists the frequently seen processes in Windows and also has a short explanation for each one.
Other Useful Resources:
- Hunt Evil Poster by SANS
- 13Cubed Windows Process Genealogy Update Video
- Core Processes in Windows System by CyberY
- Windows 10 Core Processes Video by Cyber Pro
- Core Windows Processes Room – TryHackMe
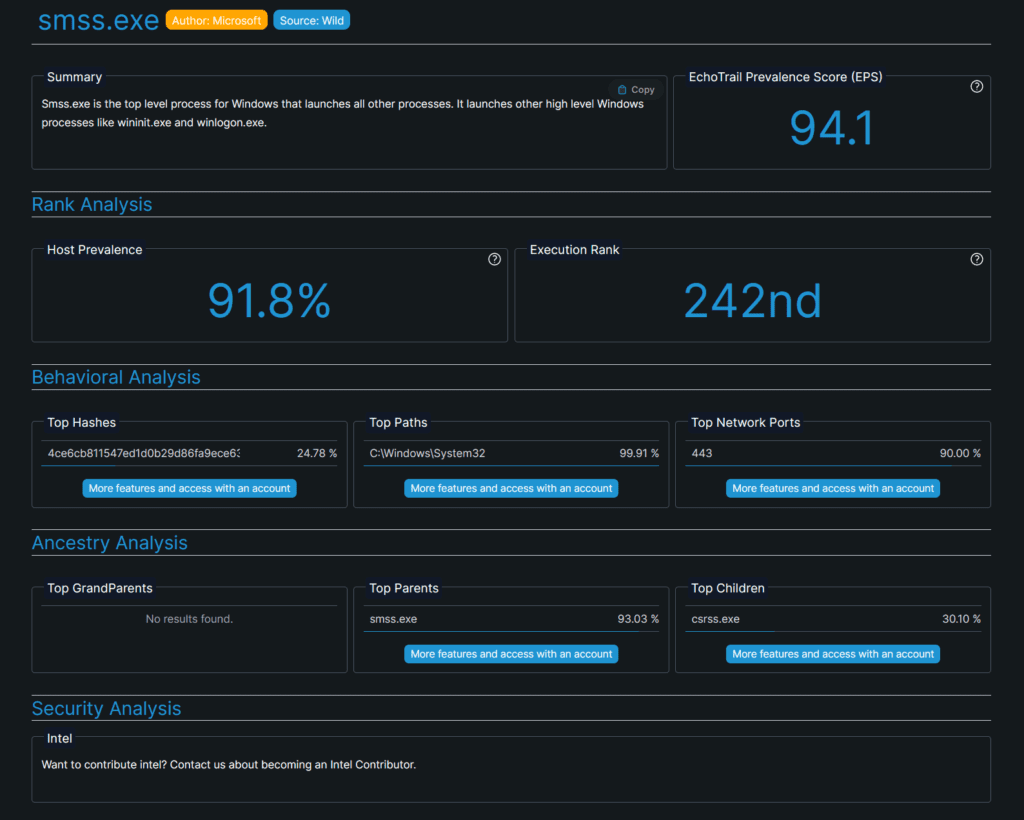
Website to Check for Windows Processes
If you encountered a process you are not sure about it, you can use this EchoTrail platform to search for any Windows process name or hash, and the website will provide you with valuable information about it such as process description, top parents, expected full path, top hashes, etc.
Conclusion
Understanding the parent-child relationships helps forensic investigators determine the relationships between processes, identify potentially malicious activity, and understand the process hierarchy within the system being analyzed. We used pstree plugin of Volatility to showcase some of process relationships.
~ Cya in the next one 🙂